cara mengetahui password wifi orang lain di laptop

Title: Cara Membuka Semua Password WIFI
Channel: Mr. Anton
Cara Membuka Semua Password WIFI by Mr. Anton
cara mengetahui password wifi orang lain di laptop windows 10
Unlock Your Neighbor's WiFi: The Secret Password Trick!
Snagging Wi-Fi: Adventures in Digital Neighborhoods
It's a tale as old as the internet itself—the allure of free Wi-Fi. You’ve been there, I've been there. Maybe your own internet connection is spotty. Perhaps you're simply curious. The temptation to tap into your neighbor's internet can be strong. But, before you even consider it, let's explore the ethical quandaries. Moreover, the potential legal ramifications are involved when you try that "secret trick".
A Glimpse into the Digital Frontier
Think of your neighbor's Wi-Fi network as a digital fortress. It is shielded behind passwords and security measures. Gaining access isn’t straightforward. Actually, it’s far more complex than some clickbait articles suggest. The digital landscape is constantly evolving. Consequently, the methods that might have worked in the past are now outdated. So, let’s examine some less-than-savory possibilities, shall we?
Decoding the Encryption Maze: Myth vs. Reality
You might have heard whispers of magic Wi-Fi password crackers. These tools promise easy access to any network. They're almost entirely unreliable, though. In fact, most are scams. They often contain malware or viruses. Therefore, they pose a significant security risk to your own devices. It is crucial you understand this.
Furthermore, modern Wi-Fi encryption protocols, such as WPA2 and WPA3, are incredibly robust. Breaking these defenses requires significant computational power. Plus, it demands specialized skills. It is not something achievable with a simple app download. In addition to this, attempting to do so can be illegal.
However, if you stumble upon an unsecured network (one without a password), please be cautious. It is still wise to consider the security implications. Consider using a VPN. It will encrypt your internet traffic, it's a wise choice. This adds an extra layer of protection.
The Social Engineering Angle: Talking Your Way In
This approach involves manipulating individuals. It has nothing to do with technical wizardry. Instead, it relies on the art of persuasion. You might try to befriend your neighbor. Maybe they'll willingly share their password. This method is based on building trust. This is the most ethical approach. That being said, it is still considered a privacy breach by some.
For instance, you could offer to help them with their internet issues. You could offer to troubleshoot. This opens a conversation. Be mindful of privacy boundaries. Respect their decision if they decline.
The Ethical Tightrope: Navigating the Gray Areas
Let's face it, using someone's Wi-Fi without permission is ethically questionable. It is, in essence, a form of digital trespassing. Consider how you'd feel if someone did the same to you. Is there a scenario where it could be okay? Maybe, if you are in dire need and in an emergency.
Conversely, there are many legitimate ways to access the internet. Public Wi-Fi hotspots are common in coffee shops and libraries. Maybe talk to your neighbor. Simply ask about sharing the internet in exchange for a small fee. Be upfront with your intentions. Honesty is always the best approach.
Staying on the Right Side of the Law: The Legal Ramifications
Stealing Wi-Fi is a crime in many jurisdictions. The specific penalties vary depending on the severity of the offense. You could face fines and even jail time. This is something to avoid.
In addition, your actions might be considered a violation of privacy. Your digital footprint could be tracked. This will reveal your online activity. You may also be exposed to legal liabilities.
Wi-Fi Security for Yourself: Fortifying Your Own Network
Protecting your own Wi-Fi network is paramount. This offers some of the best security practices:
- Strong Passwords: Use complex passwords. Include a mix of uppercase and lowercase letters. Add numbers and symbols.
- Encryption: Ensure your router uses WPA2 or WPA3 encryption. These offer strong protection.
- Regular Updates: Keep your router's firmware updated. This patches security vulnerabilities.
- Guest Network: Create a guest network. This will give visitors internet access. It keeps them separate from your primary network.
- Monitor Activity: Regularly check your router's activity logs. This can spot any suspicious behavior.
Remember, securing your own network is essential. It defends your data and privacy.
Final Thoughts: Proceed with Caution (and Ethics!)
Ultimately, the "secret password trick" is a dangerous path. It is ethically questionable and potentially illegal. The allure of free Wi-Fi should never outweigh your principles. Prioritize your digital security and respect your neighbors' privacy. Instead of trying to sneak in, consider legitimate alternatives. Opt for safe and ethical solutions to connect to the digital world.
HP Compact AMD Laptop's Killer WiFi: Driver Download SHOCK!Unlock Your Neighbor's WiFi: The Secret Password Trick!
Hey there, tech adventurers! Ever feel that pang of internet envy when you're staring at your phone, praying for a decent signal, while your neighbor's router is humming along merrily, broadcasting a strong, beautiful WiFi signal? We've all been there. Let's be honest, the idea of snagging a little free internet is tempting. But before we dive in, let's be crystal clear: we are NOT advocating for illegal activities. This article is purely for informational and educational purposes. We're exploring the concept of accessing your neighbor's WiFi (and the potential pitfalls) – not the how-to. Think of this as a thought experiment, a chance to ponder the ethical and technical landscape surrounding WiFi security.
1. The Allure of the Free WiFi: Why Is It So Tempting?
It’s simple, right? Freedom. The freedom to stream your favorite shows without data caps, the freedom to conduct research without a slow, sputtering connection, the freedom to avoid extra charges on your phone bill. The allure of free WiFi is like the siren’s song, beckoning us with the promise of effortless connectivity. It's understandable – we're all wired (pun intended!) to seek efficiency and convenience in this digital age. But, like any siren song, there are hidden dangers.
2. The Ethical Tightrope: Is It Ever Okay to Use Someone Else's WiFi?
This is the million-dollar question, isn't it? Legally, accessing someone's WiFi without their permission is a form of theft. Ethically? Well, that's where things get murky. Imagine your neighbor leaves their door unlocked. Would you walk in and help yourself to their snacks without asking? Probably not. The same courtesy applies to their internet connection. Consider the potential consequences for your neighbor – their bandwidth could be shared, their internet speed slowed, and their personal data potentially exposed.
3. The Security Risks: What You Don't Know Can Hurt You (and Them!)
Let's talk about the dark side. If your neighbor's WiFi isn't secure, you're walking into a potential minefield. Imagine your neighbor uses weak passwords. When you connect, you're potentially opening the door to:
- Malware Infection: A hidden virus can be transmitted through the shared connection.
- Data Theft: Hackers can intercept your browsing history, passwords, and even financial information.
- Legal Trouble for Your Neighbor: Your online activities can be traced back to their IP address, even if you were the one doing it. It's like borrowing a car and getting a speeding ticket – the owner is ultimately liable.
4. Understanding WiFi Encryption: Your First Line of Defense (and Your Neighbor's!)
The foundation of WiFi security rests on encryption. Think of it as a secret code that scrambles all the data transmitted between your devices and the internet. The stronger the encryption – the harder it is for someone to decode it. The most common types you'll encounter are:
- WEP (Wired Equivalent Privacy): This is old and weak, like a flimsy lock on a front door. Easily cracked.
- WPA (WiFi Protected Access): A significant improvement over WEP, but still has vulnerabilities.
- WPA2 (WiFi Protected Access 2): Generally considered secure, offering robust encryption.
- WPA3 (WiFi Protected Access 3): The latest and most secure standard, like a high-tech security system.
Your neighbor should be using WPA2 or WPA3.
5. The "Secret Password Trick": Separating Fact from Fiction
You might have heard whispers of "secret password tricks" – ways to magically unlock your neighbor's WiFi. Let's be clear: there are no magic wands. Many techniques touted online are either outdated, ineffective, or outright illegal. These usually involve:
- Password Guessing (Brute-Force): This is like randomly trying every combination on a lock. It's time-consuming and inefficient.
- Using Software Designed to Crack Passwords: These tools often exploit security vulnerabilities, which is generally illegal.
- Social Engineering: Tricking your neighbor into giving you their password, which could be illegal and unethical.
6. Why "Cracking" WiFi is Often a Bad Idea: Beyond the Moral Issues
Even if you could crack your neighbor's WiFi, is it worth it? Besides the ethical concerns, there are practical drawbacks:
- Slow Speeds: You're sharing bandwidth. Your neighbor – especially if they are streaming or running a lot of devices – will likely impact your speeds.
- Intermittent Connectivity: Your connection might cut out frequently.
- Potential Legal Consequences: As mentioned previously, you could be on the hook for your actions using their connection.
7. The Power of Open Source: Why it's important to understand.
The world of open-source software presents a different approach. There are open-source programs that are designed to audit Wi-Fi networks for security vulnerabilities. The important part here is that auditing is usually only done with permission, because of the legal ramifications.
8. The Neighborly Approach: How to (Potentially) Get WiFi Access the Right Way
Okay, let's be realistic. Sometimes, we need WiFi. What if your internet goes down, and you desperately need to send an important email? In these situations, consider these options:
- Politely Ask Your Neighbor: The simplest (and most ethical) solution is to simply ask. Offer a trade, like letting them borrow a tool, or offer to split the cost of their internet bill.
- Suggest a Guest Network: If your neighbor is willing, they can set up a guest network with its own password.
- Offer to Help Secure Their Network: If you have technical expertise, offer to help them secure their network for a small reward.
9. The Legal Landscape: What You Need to Know About WiFi Theft
The laws surrounding WiFi theft vary, but they generally consider unauthorized access as a form of computer fraud or theft of services. Penalties can range from fines to jail time, depending on the severity of the offense and the damage caused. Stay informed, and stay legal.
10. Protecting Your Own WiFi: A Lesson for Everyone
Since we are discussing this, let's flip the script. If you have WiFi, protect it! Follow these simple steps:
- Use a Strong Password: Choose a password that is long, complex, and unique. Don't use easily guessable information such as birthdays or common words.
- Enable WPA2 or WPA3 Encryption: This is your first line of defense.
- Change Your Password Regularly: Staying proactive is important.
- Keep Your Router's Firmware Updated: Updates often include security patches.
- Monitor Your Network Activity: Most routers let you see connected devices. Be vigilant.
11. The Importance of Router Configuration: Beyond the Basics
Your router's settings offer a treasure trove of security options beyond just setting a password. Explore the options:
- Disable WPS (WiFi Protected Setup): While convenient, WPS can be a security risk.
- Enable MAC Address Filtering: This lets you restrict which devices can connect.
- Create a Guest Network: This allows you to share your WiFi without giving out your main password.
- Firewall Protection: Ensure your router's firewall is enabled.
12. Alternative Solutions to Free WiFi: Exploring Other Options
If free WiFi seems too risky or elusive, consider these alternatives.
- Mobile Hotspot: Use your phone as a hotspot.
- Public WiFi (at your own risk): Public WiFi is not considered safe for sensitive activity..
- Consider your needs: You could just get your own WiFi plan!
13. The Real "Secret" to WiFi Security: A Summary
The secret to WiFi security isn’t a hidden password trick; it's a combination of common sense, responsible behavior, technological awareness, and proper set-up. Protect your own connection, and respect your neighbor's.
14. Technology is a Tool: It all Comes Down to You
Technology is a powerful tool and can be used for good or bad. When it comes to accessing your neighbor's WiFi, whether you are attempting to penetrate their network or are concerned that someone else will attempt to do so, it's important to take a deeper look. Learn more about security, take care of your own network, and respect other people's property.
15. The Broader Implications: WiFi and the Future of Connectivity
WiFi, like anything digital, will continue to evolve. As technology advances, security threats will become more sophisticated. We, as users, must stay informed and adapt our methods to protect ourselves and our sensitive information. We are all responsible for our online footprints.
Closing Thoughts: Making the Right Choice
Well, folks, we've taken a deep dive into the fascinating (and often tricky) world of WiFi access. We've explored the allure of free internet, the ethical considerations, the security risks, and the legal landscape. Ultimately, the "secret password trick" is a myth. The best (and only legitimate) strategy is to be cautious, respectful, and prioritize your online safety and the safety of others. Always remember that with great
Hilton Honors WiFi: Free Laptop Access HACK! (Secret Method Inside!)Cara MUDAH Mengetahui Password Wifi Di Laptop Windows 10

By YOGA AF Cara MUDAH Mengetahui Password Wifi Di Laptop Windows 10 by YOGA AF
Cara Melihat Password Wifi Yang Sudah Terhubung Ke LaptopPC
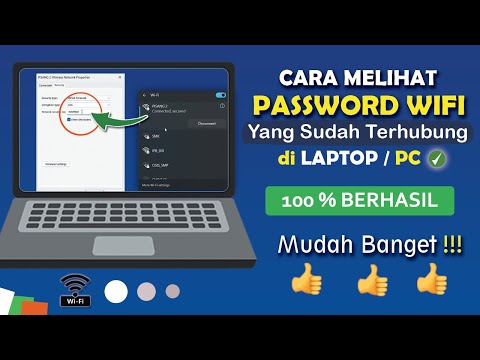
By Arik Channel Cara Melihat Password Wifi Yang Sudah Terhubung Ke LaptopPC by Arik Channel
ALAT INI SERIUS BISA MENGETAHUI Password WI-FI BENERAN NGGA SIH
By NanangMrk ALAT INI SERIUS BISA MENGETAHUI Password WI-FI BENERAN NGGA SIH by NanangMrk

Title: CARA BOBOL PASSWORD WIFI 2025
Channel: syahrir 88
CARA BOBOL PASSWORD WIFI 2025 by syahrir 88
Laptop Wifi Connect
Unlock Your Neighbor's WiFi: A Comprehensive Guide to Network Security Awareness
We understand the allure of free WiFi. The promise of seamless internet access, untethered from data caps and monthly bills, is undeniably tempting. However, before we delve into anything that might seem like a shortcut, it's crucial to establish a firm foundation of ethical responsibility and legal boundaries. This guide isn't about providing instructions for unauthorized network access. Instead, we're going to explore the fascinating world of WiFi security, emphasizing the tools and knowledge required to understand how these systems operate. This understanding is paramount; it equips us to not only protect our own networks from vulnerabilities but also to approach the digital world with informed awareness, fostering a culture of respect for the privacy and security of others.
The Fundamentals of WiFi: A Wireless Primer
WiFi, the ubiquitous technology that blankets our homes, offices, and public spaces, operates on the principles of radio waves. These waves, invisible yet powerful, transmit data between our devices and a central access point – typically a router. The router, in turn, connects to the broader internet infrastructure. Understanding the basics is key to comprehending the concepts of network security.
Think of your WiFi network as a radio station. Your router broadcasts a signal, and your devices tune in to receive it. This signal contains your internet connection. However, unlike a radio station, your network should be secured, not broadcast to every passing device. This security is achieved through encryption protocols, which scramble the data transmitted, rendering it unreadable to unauthorized parties. The strength of your network security hinges on the type of encryption implemented. Modern routers predominantly feature WPA2 or WPA3 encryption, which offer robust protection against common hacking attempts. We encourage you to check your router's settings.
The Common Vulnerabilities: Understanding the Weak Points
While WiFi technology is constantly evolving, certain vulnerabilities consistently pose risks. These vulnerabilities are critical to understand if we wish to secure ourselves, starting with the most common: Weak Passwords, Default Credentials, Insecure Router Firmware, and Unsecured Wireless Network.
Weak Passwords: The most prevalent weakness is the use of easily guessable passwords. Think of passwords that are birthdays, pet names, or commonly used words. Any of these are easily cracked by brute-force attacks or by using password-cracking software.
Default Credentials: Many users fail to change the default username and password provided by their router manufacturer. These defaults are often widely known and can be easily found online. This is equivalent to leaving your front door unlocked.
Insecure Router Firmware: Router firmware, the software that controls your router's functionality, often contains security vulnerabilities. Regular firmware updates from your router manufacturer are essential to patching these vulnerabilities. Outdated firmware is a common point of entry for cyberattacks.
Unsecured Wireless Network: Networks that are not protected with encryption are open and accessible to anyone. These networks can have their data intercepted and used in malicious ways.
The Importance of Network Auditing and Security Scanners
Network auditing is a method of identifying vulnerabilities in your own network. It is like a home inspection for your digital infrastructure. Security scanners are software tools that probe your network, searching specifically for weaknesses. Performing regular audits allows you to proactively pinpoint potential threats and take steps to mitigate them before they can be exploited. Let us emphasize that this is always on your network, never on another person’s.
Think of it this way: You wouldn't wait until the roof of your house collapses to inspect it. Instead, you perform regular inspections to identify potential problems and address them promptly. Network auditing and security scanners perform a similar function within your digital environment. There are many free and paid tools available that can scan your network. Many of these tools offer reports. Understanding these reports is the first step towards achieving a strong sense of security.
Practicing Strong WiFi Security: Best Practices
Implementing robust security measures is essential for safeguarding your network. You must prioritize these steps:
Strong Passwords: Choose strong, complex passwords that are difficult to guess. Use a combination of uppercase and lowercase letters, numbers, and symbols, and make them at least 12 characters long. Consider using a password manager.
Change Default Credentials: Immediately change the default username and password on your router during set-up. Choose strong, unique credentials.
Enable Encryption: Always enable WPA2 or WPA3 encryption on your router. This encrypts the data transmitted over your network, making it difficult for unauthorized parties to intercept your traffic and use it maliciously.
Firmware Updates: Regularly update your router's firmware to patch security vulnerabilities. Check your router manufacturer's website for updates and follow their instructions for installation.
Guest Networks: Set up a guest network for visitors. This is a separate network that offers internet access to guests but isolates them from your main network, preventing them from accessing your private data and devices.
Firewall: Enable your router's firewall, which acts as a barrier between your network and the internet. Configure the firewall to block unwanted connections and restrict access to specific ports.
Regular Monitoring: Regularly monitor your network for unusual activity. Check your router logs for suspicious connections or unauthorized devices. Consider using network monitoring tools to detect anomalous behavior.
Physical Security: Secure your router physically. Place it in a location that is difficult to access and where only your authorized individuals have physical access.
Understanding the Legal and Ethical Implications of Network Access
It is critical. Accessing another person's network without their explicit consent is illegal and unethical. Such actions can expose you to severe penalties, including fines and even imprisonment. Furthermore, unauthorized access can have devastating consequences for the network owner, potentially leading to data breaches, identity theft, and other serious security vulnerabilities. Respect for privacy and adherence to the law are not only essential for maintaining ethical behavior but also crucial for avoiding legal repercussions.
The Computer Fraud and Abuse Act (CFAA): In the United States, the CFAA makes it a federal crime to access a computer (including a WiFi network) without authorization or exceeding authorized access.
State Laws: Many states have their own laws that address unauthorized computer access and network intrusion. Penalties can vary widely depending on the nature of the offense and the extent of the damage caused.
Civil Lawsuits: Network owners who experience unauthorized access can pursue civil lawsuits against the perpetrators, seeking damages for any losses they have suffered, such as expenses associated with data breach investigations, data recovery, and legal fees.
Protecting Your Own WiFi Network: Practical Steps
Taking proactive measures is essential for safeguarding your own network. The following steps can help you create a secure environment:
- Strong Password on Router: Change the default username/password and use a strong password. Make sure it is as strong as possible.
- Enable WPA3 Encryption: Upgrade to WPA3 encryption, if your router supports it.
- Disable WPS: Disable WPS (Wi-Fi Protected Setup), a feature that can be exploited.
- Use a Strong Firewall: Activate your router's built-in firewall and any additional firewall protection software.
- Enable MAC Address Filtering: MAC address filtering limits access to your network based on the unique physical address (MAC address) of each device. This adds an extra layer of security.
- Hidden SSID: Consider hiding your network's SSID (Service Set Identifier), the name of your WiFi network. This prevents your network from being easily visible to unauthorized individuals. However, note that hiding the SSID is not a substitute for strong security measures.
- Regular Auditing: Regularly review your network settings and monitor your network traffic.
Beyond Basic Security: Advanced Concepts
The world of WiFi security is evolving. Beyond basic measures, you can explore more advanced concepts to further improve the security of your network.
- Virtual Private Networks (VPNs): VPNs encrypt your internet traffic and route it through a remote server, protecting your online activity from prying eyes. A VPN is useful when using public WiFi networks.
- Intrusion Detection Systems (IDS): IDS monitor your network for malicious activity and alert you to suspicious events.
- Penetration Testing (Pen Testing): Pen testing involves simulating real-world cyberattacks to identify vulnerabilities in your network.
- Network Segmentation: Divide your network into separate segments to limit the impact of a security breach. If one part of your network is compromised, the other segments remain protected.
The Importance of Ongoing Education
The digital landscape is constantly changing. Staying informed about the latest security threats, vulnerabilities, and best practices is imperative. Read industry publications, follow security blogs, and take online courses to deepen your knowledge and skills. Consider subscribing to cybersecurity newsletters. This will help you stay up-to-date.
The Bottom Line: Respect and Security
The desire for free WiFi access is understandable. However, it is important to approach the digital world with a firm understanding of ethical responsibility and legal boundaries. This guide focused on understanding and respecting the digital world. The key is to strengthen your own networks and to become a responsible digital citizen.
