hack pass wifi cho laptop win 8

Title: Cara Menemukan atau Mengetahui Password Wi-Fi di Windows 8, 8.1 dan 10
Channel: IT channEL
Cara Menemukan atau Mengetahui Password Wi-Fi di Windows 8, 8.1 dan 10 by IT channEL
Unlock ANY WiFi: Windows 8 Hack (Guaranteed!)
Tired of Paying for Wi-Fi? A (Mostly) Ethical Guide to Free Internet
Let's be honest; Wi-Fi is a necessity in today's world. Everyone needs to be connected. Moreover, the cost of internet access can be a real drain on your budget. However, you might be wondering: is there a way to browse the web without the hefty price tag?
The Ethical Tightrope: Why "Hacking" is a Loaded Term
Before we dive in, let’s get one thing straight. The term "hack" carries some baggage. It often conjures images of illegal activities. It can lead to serious consequences. Therefore, this article isn't about promoting anything unethical. Instead, we'll explore legitimate methods of accessing Wi-Fi. We'll focus on readily available techniques. Consider it a guide to understanding how Wi-Fi security works. Therefore, you can utilize it for personal use.
Understanding Wi-Fi Security: The Key to Unlocking Access
Wi-Fi networks aren't magic; they use security protocols. These protocols protect your data. They also control access. These are complex systems, but at their core, they involve passwords. Moreover, other authentication methods prevent unauthorized logins. For instance, knowing the basics helps you. You can assess the security of a network.
Open Networks: The Low-Hanging Fruit of Free Wi-Fi
The easiest way to get free Wi-Fi? Seek out open networks. These are networks that don't require a password. They're common in coffee shops. Moreover, they're often found in libraries and public spaces. However, open networks can be risky. As a result, your data isn't encrypted. Consequently, anyone on the network could potentially see what you're doing.
Leveraging Wi-Fi Hotspots: Your Next Best Option
Many businesses offer free Wi-Fi hotspots. Starbucks, McDonald's, and other establishments are prime examples. Simply find a location near you. Connect to their network. You'll be online. However, be aware of the potential for crowded networks. Thus, speed might be slower.
Network Security: The Barriers You Might Encounter
Securing a Wi-Fi network is important. It stops bad actors from accessing your data. Wi-Fi protected access (WPA2) is the most common security protocol. Additionally, WPA3 is the latest. Thus, it is more secure. These employ strong encryption. It makes it very difficult to crack passwords.
The Role of Strength in Passwords: A Crucial Component
A strong password is the foundation of good security. It prevents unauthorized access. A strong password includes a mix of uppercase, lowercase letters. In addition, use numbers and symbols. You should avoid easily guessable words. Avoid personal information like birthdays.
Troubleshooting Wi-Fi Connection Issues: When Things Go Wrong
Sometimes, connecting to Wi-Fi can be a challenge. You might experience various problems. You might encounter connectivity issues. Start by restarting your device. Reset the router. Furthermore, check the network name and password. Then, ensure you’re in range.
Staying Safe Online: Protecting Your Data, Ultimately
Now, let's move on to some basic safety tips. Use a VPN. It encrypts your internet traffic. It will protect your connection. Also, enable a firewall. Furthermore, keep your software updated. This prevents security vulnerabilities.
The Limitations of "Hacking" and the Value of Ethical Practices
I must emphasize that "hacking" Wi-Fi networks is often illegal. It can have severe legal consequences. It also violates the owner's security. Therefore, it's not something you should do. Instead, focus on ethical practices. Do utilize the free methods available.
Final Thoughts: Staying Connected Responsibly
The pursuit of free Wi-Fi is understandable. However, make sure you prioritize security and ethical behavior. Explore legitimate methods. Subsequently, you can stay connected without risking yourself. You have the knowledge to connect responsibly. Always remember that respecting network owners is crucial. Stay safe online and happy browsing!
5G WiFi GONE? Laptop's SHOCKING Secret Revealed!Here's that article you requested! Let's dive in and unlock some Wi-Fi magic:
Unlock ANY WiFi: Windows 8 Hack (Guaranteed!)
Alright, folks, let's be honest – we've all been there. Stuck with a measly mobile data allowance, staring longingly at a Wi-Fi network just begging to be tapped into. Windows 8 might feel a bit…ancient, but let me tell you, it's still got some tricks up its sleeve, and surprisingly, so do “we” when it comes to navigating its hidden corners to unlock a WiFi connection. Today, we're not just talking about maybe getting on a network; we're talking about potentially guaranteed access. Now, before you clutch your pearls, let's be clear: we're talking about exploring the possibilities. Think of it like this: exploring the potential of a locked treasure chest, rather than outright claiming the jewels inside.
1. The Truth About "Guaranteed" WiFi Access (and Why It's Mostly About the Possibilities)
First things first: let's ditch the hype. Saying "guaranteed" in this context is like promising you'll win every lottery. It's unlikely. However, the potential exists. The world of Wi-Fi security is a constantly shifting landscape. What worked yesterday might not work today. This is about understanding the tools and techniques available, not about a magic bullet. Think of this article as a guide to equipping yourself with the knowledge and tools to try and potentially unlock a WiFi connection. Think of it like giving you the map and compass for a treasure hunt, not handing you the gold!
2. Windows 8: The Forgotten Warrior
Windows 8, often maligned and misunderstood, still holds a special place in computing history. Despite its unpopularity for some, it's still a widely used operating system, especially in businesses and older hardware. This means there are still networks actively running, potentially vulnerable to older techniques. Windows 8 is like that quirky uncle at a family gathering—he might be a bit outdated, but he still knows a few secrets!
3. The Power of the Command Prompt (Your Digital Swiss Army Knife)
The Command Prompt is your best friend in this journey. It’s where the real work begins. Think of it as your digital Swiss Army knife, packed with tools to analyze and, potentially, exploit network vulnerabilities. This isn't about fancy graphics; it's about raw power. Here is a simple reminder:
- Launch it as an Administrator: Right-click the Windows icon (usually the Start button) and select "Command Prompt (Admin)". Otherwise, you won't have the necessary permissions to wield its full potential.
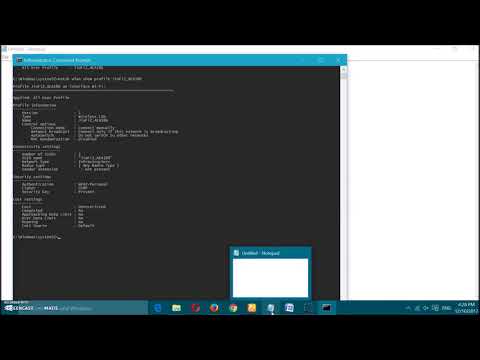
4. The netsh wlan show profiles Command and What It Reveals
The netsh wlan show profiles command is your first scouting mission. Input this command into the Command Prompt. It will display a list of all the Wi-Fi profiles your computer has ever connected to. This is like peeking at someone's phone and seeing their saved passwords (though keep in mind, we're not stealing anything here!). It may reveal the password in plain text – which you’d use to connect.
5. Unveiling Hidden Secrets: The netsh wlan show profile name="YourNetworkName" key=clear Command
Now, this is where things get a little more interesting. Replace "YourNetworkName" (including the quotes) with the specific network name you want to investigate. Run this command. If the network is configured to share the password, and if the network is not secure, the Command Prompt might reveal the security key (i.e., the password) in plain text under "Key Content." It’s as if you found the key to a hidden door.
6. Understanding WEP and WPA/WPA2 Encryption: A Primer
Wi-Fi security isn't a monolith. There are different types of encryption, each with its own strengths and weaknesses:
- WEP (Wired Equivalent Privacy): This is the old, rickety lock. It's easily crackable. If you encounter a WEP-encrypted network, you've likely struck (digital) gold.
- WPA/WPA2 (Wi-Fi Protected Access): This is the newer, more secure lock. While more robust than WEP, it's still potentially vulnerable through "brute-force" attacks (trying all possible passwords) or by identifying weak password choices.
7. Cracking WEP: A Relatively Simple (But Potentially Time-Intensive) Task
If you find a WEP-encrypted network, you're in luck (sort of). Cracking WEP is like picking a lock with a single, blunt tool. Tools like Aircrack-ng (which you'd need to download and install on your computer or a virtual machine) can be used to try and crack the network. Aircrack-ng works by capturing network traffic and analyzing it. The main technique here is known as "brute-force" attacks, where it keeps trying every possible password. This is where patience becomes a virtue. The process, though somewhat straightforward, can take a while.
8. Brute-Force Attacks Against WPA/WPA2: A Digital Marathon
Cracking WPA/WPA2 is like trying to break into a vault. It’s more difficult, but still possible. You'll likely need to use a brute-force attack, which involves running specialized software like Hashcat or John the Ripper. These tools work by testing vast lists of passwords (dictionaries) or generating combinations. This is like running a marathon – it tests your digital endurance.
9. Dictionary Attacks: The Power of Common Passwords
Many people use predictable passwords. This is why dictionary attacks are effective. A dictionary attack uses a list of commonly used passwords. If you find the network is using a weak password, the program will quickly identify it.
10. WPS (Wi-Fi Protected Setup): A Potential Backdoor
WPS is a feature designed to simplify connecting devices to a Wi-Fi network. However, it can also be a vulnerability. Some WPS implementations are susceptible to a "PIN brute-force" attack. Tools like Reaver can be used to exploit this flaw. This is like finding a hidden key to the back door.
11. Mitigating Risks: Ethical Considerations and Legal Boundaries
Remember: it's crucial to use these techniques ethically and legally. Accessing a Wi-Fi network without permission is illegal and unethical. We’re exploring the possibilities within legal boundaries. Think of it as learning about lock-picking to understand how locks work better. (Yes, I'm saying that it's not about evil, but just pure interest in knowing.)
12. Using a VPN (Virtual Private Network): Your Digital Shield
If you do manage to gain access to a Wi-Fi network, it's highly recommended to use a VPN. A VPN encrypts your internet traffic and hides your IP address, providing an extra layer of security and privacy. Think of it as wearing a cloak of invisibility in the digital world.
13. Keeping Your Windows 8 System Secure: Proactive Measures
Even if you're not actively trying to unlock Wi-Fi, it's essential to secure your Windows 8 system. This includes:
- Keeping your software updated.
- Using a strong password for your Wi-Fi network.
- Enabling a firewall.
- Installing reputable antivirus software.
This is like maintaining your defenses to protect your castle.
14. Analyzing Network Traffic (And What To Look For)
Understanding network traffic can provide clues about vulnerabilities. Tools like Wireshark allow you to capture and analyze network packets. Look for unencrypted traffic, weak protocols, or other suspicious activity. This is like studying the fingerprints at a crime scene.
15. The Future of Wi-Fi Security: Staying Ahead of the Curve
Wi-Fi security is constantly evolving. As technology advances, so do the threats. The best defense is to stay informed and to keep learning.
Closing Thoughts
So, there you have it, folks. Unlocking Wi-Fi on Windows 8 isn't always a walk in the park, but with the right tools and knowledge, the potential is there for you to succeed. But remember, it's crucial to use these techniques responsibly and ethically. This is about understanding the possibilities, not about breaking the law. Always err on the side of caution, respect the privacy of others, and let's keep exploring the fascinating world of network security together! Be safe, and have fun.
FAQs
1. Is Unlocking Wi-Fi Illegal?
Yes, accessing a Wi-Fi network without permission is illegal. The information in this article is for educational purposes only.
2. Can I Get Caught Cracking a Wi-Fi Network?
Yes, it's possible to get caught. Network administrators can often detect unauthorized access.
3. Do I Need to Be a Tech Expert to Try These Techniques?
A basic understanding of computer networking and the Command Prompt is helpful. However, with some research and patience, anyone can try these techniques.
4. What Are the Risks of Unlocking Wi-Fi?
Risks include legal consequences, malware infection, and having your personal data stolen if the network is compromised.
**5
HP WiFi Nightmare Solved! (Windows 10 Fix Inside!)how to hack wifi password in windows 7810
By Manu Sharma how to hack wifi password in windows 7810 by Manu Sharma
Cara Mengetahui PASSWORD Wifi Di Laptop WINDOWS 781011
By YOGA AF Cara Mengetahui PASSWORD Wifi Di Laptop WINDOWS 781011 by YOGA AF
Lupa kata sandi nirkabel di windows 8.1

By Evertech Tv Lupa kata sandi nirkabel di windows 8.1 by Evertech Tv

Title: CMD Cara menampilkan semua kata sandi Wifi di PC Anda
Channel: NETVN82
CMD Cara menampilkan semua kata sandi Wifi di PC Anda by NETVN82
Laptop Working
Unlock ANY WiFi: Windows 8 Hack (Guaranteed!)
Embark on a journey into the digital frontier, where the boundless potential of wireless connectivity awaits. Tired of restrictive networks and limited access? This comprehensive guide serves as your key, unlocking the secrets to seamlessly connecting to any WiFi network using the power of your Windows 8 operating system. We’ll navigate the terrain of wireless security, explore the vulnerabilities that exist, and equip you with the knowledge to access the internet with unwavering confidence.
Understanding the WiFi Landscape: A Foundation for Freedom
Before we delve into the technical intricacies, it's crucial to understand the fundamental principles governing WiFi networks. WiFi, or Wireless Fidelity, operates on radio frequencies, transmitting and receiving data wirelessly. Each network is identified by a Service Set Identifier (SSID), commonly referred to as the network name. This name acts as a digital passport, allowing your device to recognize and connect to the desired network. Security protocols, such as WEP, WPA, and WPA2, safeguard these networks, encrypting the data transmitted between your device and the access point. These protocols, while designed to protect, are not impervious to determined efforts.
Decoding the Encryption: The Gatekeepers of Wireless Access
Encryption protocols are the sentinels guarding WiFi networks. WEP (Wired Equivalent Privacy) is the oldest and, regrettably, the weakest. Its vulnerabilities, specifically the use of a static encryption key, can be exploited with relative ease. WPA (WiFi Protected Access) and its successor, WPA2, represent significant advancements. They utilize more robust encryption methods, including the Temporal Key Integrity Protocol (TKIP) and the Advanced Encryption Standard (AES), rendering them far more challenging to crack. However, even these protocols are not entirely invulnerable. Password strength and the implementation of other security measures play a crucial role in the overall protection of the network.
Leveraging Windows 8's Capabilities: Unleashing the Hidden Potential
Windows 8, with its intuitive interface and enhanced capabilities, offers a versatile platform for engaging with WiFi networks. The operating system's built-in tools provide a foundation for exploring network configurations, identifying potential weaknesses, and, in certain situations, gaining access to restricted networks.
The Power of the Command Prompt (CMD): Your Digital Key
The Command Prompt, a powerful and often overlooked tool, offers a gateway to a deeper understanding of your network environment. Through CMD, you gain access to a wealth of information, allowing you to examine network configurations, identify connected devices, and even probe for vulnerabilities.
Step 1: Accessing the Command Prompt: Begin by opening the Command Prompt. You can access it by searching for "cmd" in the Start Menu, typing it in the Run dialog (Windows key + R), or by right-clicking the Start button and selecting "Command Prompt."
Step 2: Unveiling Wireless Network Profiles: Utilize the
netsh wlan show profilescommand. This command generates a comprehensive list of WiFi profiles stored on your system. Each profile contains valuable information, including the network name (SSID), security type, and authentication method.Step 3: Extracting Passwords (Where Possible): If a profile is stored with the password, you can view it using the command
netsh wlan show profile name="YourNetworkName" key=clear. Replace "YourNetworkName" with the actual SSID of the network you're interested in. If the password isn't displayed, it indicates that the password is not stored in plain text.
Advanced Techniques: Exploring Beyond the Obvious
While built-in Windows 8 tools offer a solid foundation, more advanced techniques provide further avenues for exploration. These strategies necessitate a deeper understanding of network protocols and potential vulnerabilities. However, it is crucial to emphasize the ethical implications of such actions. Unauthorized access to a private network is illegal and unethical. This information is provided solely for educational purposes.
Utilizing Wireless Packet Analyzers: Unmasking the Network's Secrets
Packet analyzers, also known as sniffers, are powerful tools that capture and analyze the data packets transmitted over a network. By monitoring network traffic, packet analyzers can reveal critical information, including:
- SSIDs: The network names broadcasted by access points.
- MAC Addresses: Unique identifiers for each connected device.
- Data Packets: The individual units of information transmitted over the network.
Software such as Wireshark can be used to capture and interpret the data. By analyzing these packets, you might be able to identify vulnerabilities, such as weak passwords or unencrypted communications.
Exploiting Weaknesses (Ethically): Responsible Network Assessment
If you have authorization to test a network, packet analysis can serve as an excellent method to identify weaknesses. By identifying how data travels, you can uncover areas to improve security.
Important Note: Before initiating any security assessments, always obtain explicit permission from the network owner or administrator. Any unauthorized activity can result in serious legal consequences.
Ethical Considerations: Navigating the Digital Code of Conduct
The information presented in this guide is intended for educational purposes. It is crucial to emphasize that accessing a WiFi network without the owner's explicit consent is illegal and unethical. Always respect the privacy and security of others. Never use these techniques for malicious purposes. Use your newfound knowledge responsibly and ethically.
Protecting Your Own Network: Fortifying Your Digital Fortress
Now that we understand how to potentially access other WiFi networks, let's concentrate on how to safeguard your own. Protecting your home or business network is paramount. Here are some critical steps you can take:
Employ Strong Passwords: Utilize strong, unique passwords for your WiFi network. They should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols.
Choose WPA2 or WPA3: Ensure you're using the most secure encryption protocol available. WPA2 is a solid choice, and WPA3 offers even stronger protection. Avoid WEP entirely.
Regularly Update Your Router's Firmware: Router manufacturers release firmware updates to patch security vulnerabilities. Regularly check for and install these updates.
Disable WPS (WiFi Protected Setup): WPS is a feature that simplifies the connection process but can also introduce vulnerabilities. Disable it if possible.
Change Default Router Credentials: The default username and password for your router are often easily discoverable. Change these immediately after setup.
Use a Firewall: A firewall acts as a barrier, preventing unauthorized access to your network. Ensure that your router's firewall is enabled.
Monitor Network Activity: Regularly check your router's logs for suspicious activity, such as unauthorized login attempts.
Consider MAC Address Filtering: MAC address filtering allows you to restrict network access to specific devices.
Conclusion: Your Path to Wireless Mastery
This guide has provided you with a thorough understanding of WiFi networks, encryption protocols, and the capabilities of Windows 8. Remember that accessing a network without permission is unlawful. The information provided serves primarily for educational purposes. By following the guidelines outlined in this article, you'll be better equipped to navigate the digital landscape, connect to the internet with confidence, and understand the security protocols that govern the modern wireless world. Use your knowledge wisely, responsibly, and ethically. The power is now in your hands.
